Today’s Patent – Lateral Movement Detection for Network Security
As cyber threats continue to evolve, so must our defenses. In today’s interconnected digital landscape, a traditional firewall or antivirus system is no longer enough. Enterprises need robust tools that go beyond surface-level scans and proactively detect suspicious behavior hidden deep within network traffic. One such advancement is the patented technology behind Lateral Movement Detection for Network Security Analysis, granted as US Patent US10015177B2 on July 3, 2018. This invention is credited to Sudhakar Muddu, Christos Tryfonas, Fumei Lam, and Georgios Apostolopoulos, and is currently assigned to Splunk Inc., a leader in cybersecurity and data analytics.
🔐 What Is Lateral Movement in Cybersecurity?
In the context of cybersecurity, lateral movement refers to the actions a threat actor takes after gaining access to a system—typically moving through the network to access critical data or escalate privileges. These movements often go unnoticed, as attackers use valid credentials and appear to operate like legitimate users.
Detecting lateral movement is one of the most important and challenging aspects of network security analysis. Attackers can linger within an organization’s system for weeks or even months, quietly harvesting data and escalating access. That’s where this patented innovation plays a crucial role.
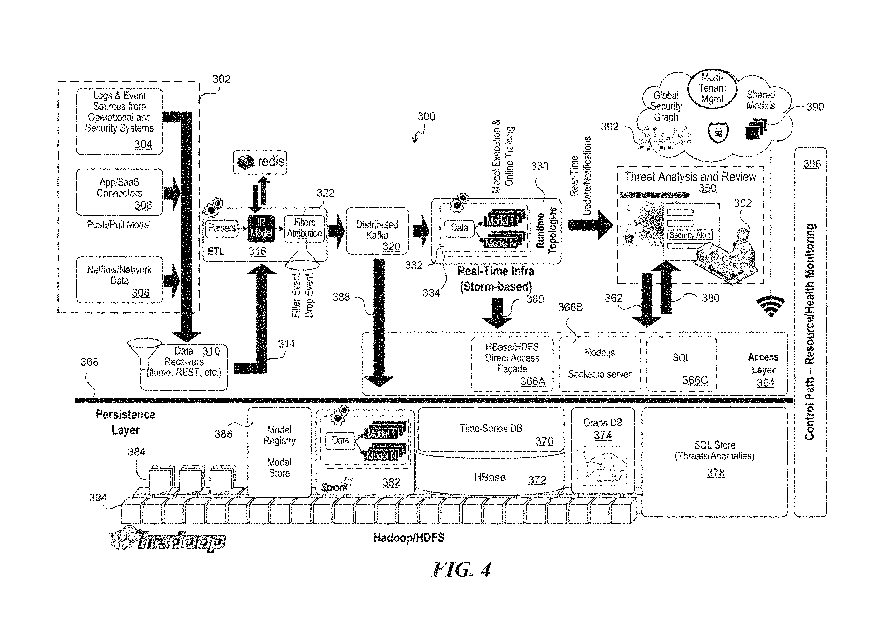
🧠 Inside the Patent: How It Works
The patented system utilizes a computer-implemented method that continuously monitors network activity data. Instead of focusing solely on known malware signatures or external threats, it analyzes user behavior, device interactions, and communication paths across a network.
Here’s what makes it stand out:
- 📊 Usage Relationship Analysis: It builds patterns based on how users typically interact with devices on the network.
- 🧭 Similarity Scores: The system calculates behavioral similarity ratings to flag unusual actions.
- 🚨 Real-Time Threat Response: When suspicious movement or unexpected device access is detected, the system immediately initiates alerts or countermeasures.
This allows for early breach detection, even when the attacker uses legitimate credentials or moves slowly to avoid suspicion.
🛡️ The Need for Intelligent Network Security
Most traditional security appliances (like firewalls or intrusion detection systems) operate based on rule sets or known signatures. While useful, they have limitations:
- ❌ They cannot easily detect new or evolving threats.
- ❌ They rely heavily on predefined rules.
- ❌ They struggle under the load of growing network traffic.
- ❌ Manual upgrades are time-consuming and costly.
As businesses adopt cloud technologies and remote work models, the number of endpoints and network traffic volume has surged, exposing more vulnerabilities. A system that adapts and learns from usage data, like this one, fills the critical gap between reactive and proactive defense.
🧩 Use Cases in Modern Enterprises
The Lateral Movement Detection for Network Security Analysis technology is especially useful for:
- 🏢 Enterprise IT Departments – to detect insider threats or compromised accounts.
- 🏥 Healthcare Networks – where patient data privacy must be strictly maintained.
- 💳 Financial Institutions – to prevent unauthorized access to sensitive financial data.
- ☁️ Cloud Infrastructure – for detecting unusual access patterns across virtual machines or hybrid systems.
By using real-time behavioral analytics, this system provides actionable insights that enable IT teams to shut down potential breaches before they escalate.
🔍 Why Behavioral-Based Detection Matters
Behavioral-based security solutions have rapidly gained traction in the cybersecurity world. Instead of simply identifying known threats, these systems create a dynamic profile of normal user behavior and detect deviations from that norm.
In this patented method, the system monitors:
- Login patterns
- Device access history
- Data retrieval and sharing frequency
- Internal communication flows
Even small anomalies—such as a user accessing a server they’ve never touched before—can trigger alerts. This intelligent pattern detection drastically shortens the time it takes to identify and respond to breaches.
⚙️ Integration with Modern Security Platforms
Given that the patent is assigned to Splunk Inc., a global leader in data analytics and cybersecurity, this technology can be seamlessly integrated into larger SIEM (Security Information and Event Management) platforms. By combining event logs, real-time alerts, and user behavior analytics, companies can achieve a holistic security posture.
Moreover, machine learning models can be layered on top of this technology to refine detection algorithms, reduce false positives, and adapt to evolving user behavior over time.
🔮 Future-Proofing Network Defense
As threat actors become more sophisticated, security systems must evolve. Lateral Movement Detection for Network Security Analysis is not just a tool—it represents a shift in how we approach cybersecurity. Instead of chasing threats, we identify the paths they might take and shut them down proactively.
This kind of behavioral intelligence is essential for:
- Reducing breach dwell time
- Complying with data protection regulations
- Protecting customer trust and reputation
- Saving millions in potential data breach costs
✅ Conclusion
This patented invention isn’t just about reacting to cyberattacks—it’s about outsmarting them. By focusing on lateral movement detection, organizations gain a powerful layer of defense that identifies intruders from within and acts before they can cause real harm.
If you’re a cybersecurity professional, network engineer, or IT strategist, this innovation highlights how next-gen security is rooted in behavioral analysis, not just firewalls and signatures.
Stay updated with Today’s Patent to discover more innovations that are shaping the future of digital defense, data privacy, and intelligent technologies.

 +1 888 890 6411
+1 888 890 6411